The last line of defense
mimx is an active-deception platform for early breach detection. If your defenses are bypassed, deep fake data created by mimx entices adversaries to give away their presence.
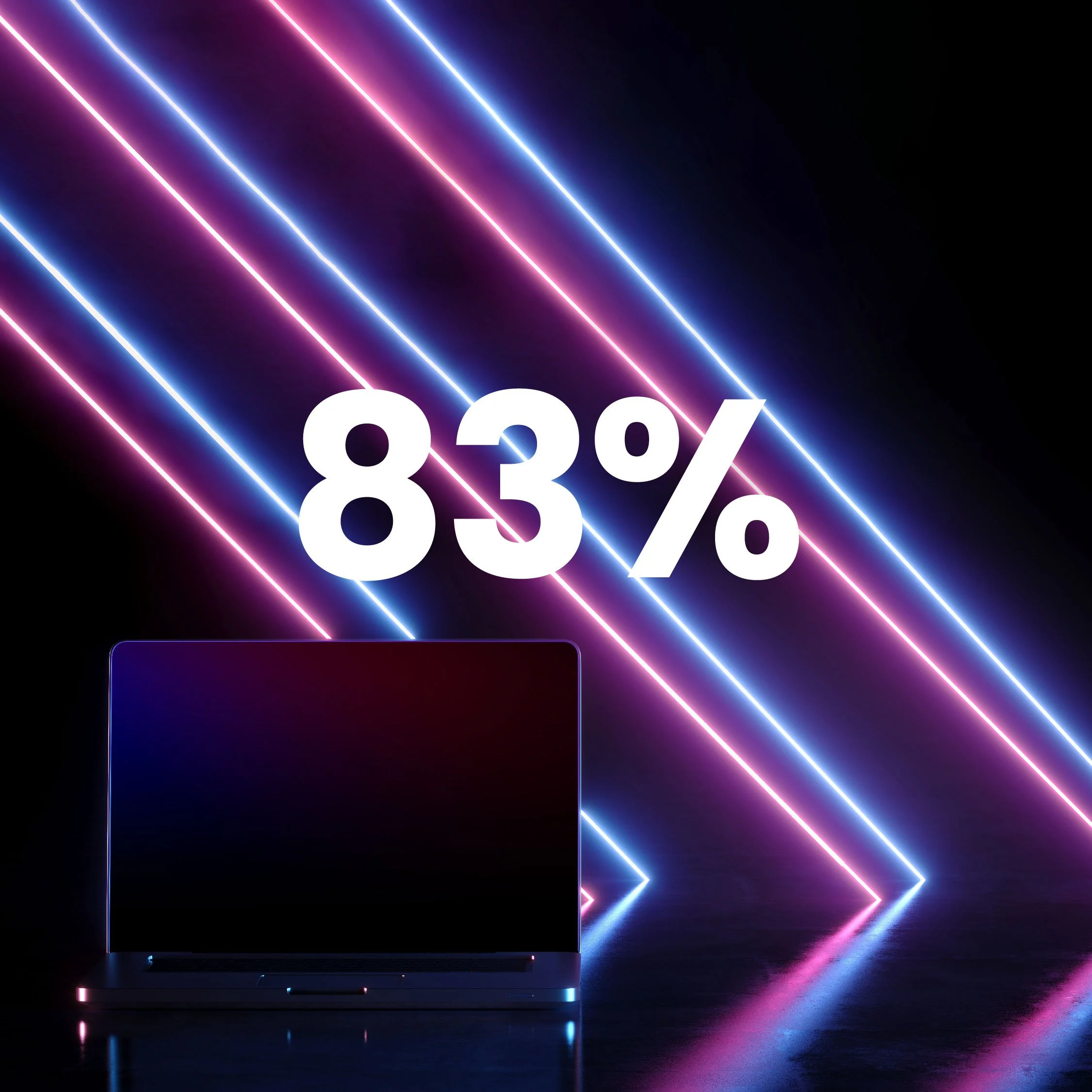
A breach is inevitable for most organizations
Defense teams must focus all their resources on preventing breaches because data should never be left unprotected. But for 83% of companies, it’s not if a data breach will happen, but when.*
*Cost of a Data Breach 2022 Report, IBM
How long would it take you to catch an intruder?
Dwell time is the duration an adversary remains undetected in an organization's systems. Ideally, that time would be measured in moments. But the average time an attacker dwelled in 2021 was 21 days.*
*M-Trends 2022, Mandiant
The fastest breach detection in the world
mimx reduces attack dwell time to moments. It creates alluring deep fake data objects indistinguishable from those created by valid users and attracts cyber criminals into engaging with them. As we call it, phishing the phisher.
Deceptive Quotations